Internetworking elements:
The diagram shows elements of a typical network, including devices, media, and services, tied together by rules, that work together to send messages. We use the word messages as a term that encompasses web pages, e-mail, instant messages, telephone calls, and other forms of communication enabled by the Internet.
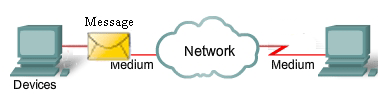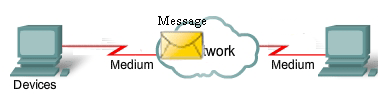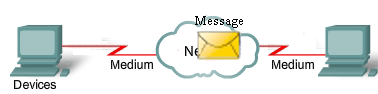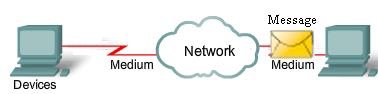
- Rules
- Medium
- Messages
- Devices
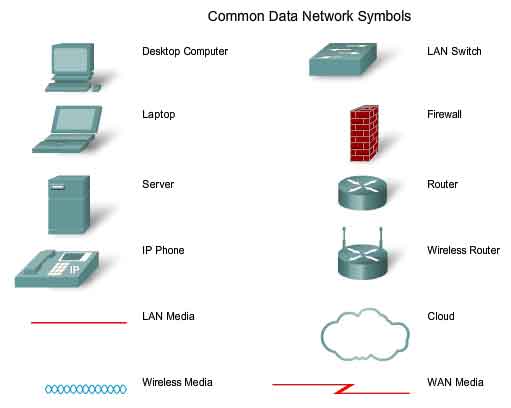
Internetworking is a very graphically oriented subject, and icons are commonly used to represent networking devices. On the left side of the diagram are shown some common devices which often originate messages that comprise our communication. These include various types of computers (a PC and laptop icon are shown), servers, and IP phones. On local area networks these devices are typically connected by LAN media (wired or wireless). The right side of the figure shows some of the most common intermediate devices, used to direct and manage messages across the network, as well as other common internetworking symbols. Generic symbols are shown for:
-
Switch - the most common device for interconnecting local area networks
- Firewall - provides security to networks
- Router - helps direct messages as they travel across a network
- Wireless Router - a specific type of router often found in home networks
- Cloud - used to summarize a group of networking devices, the details of which may be unimportant to the discussion at hand
- Serial Link - one form of WAN interconnection, represented by the lightning bolt-shaped line
Network Interface Card - A NIC, or LAN adapter, provides the physical connection to the network at the PC or other host device. The media connecting the PC to the networking device plugs directly into the NIC.
Physical Port - A connector or outlet on a internetworking device where the media is connected to a host or other networking device.
Interface - Specialized ports on an internetworking device that connect to individual networks. Because routers are used to interconnect networks, the ports on a router are referred to network interfaces.
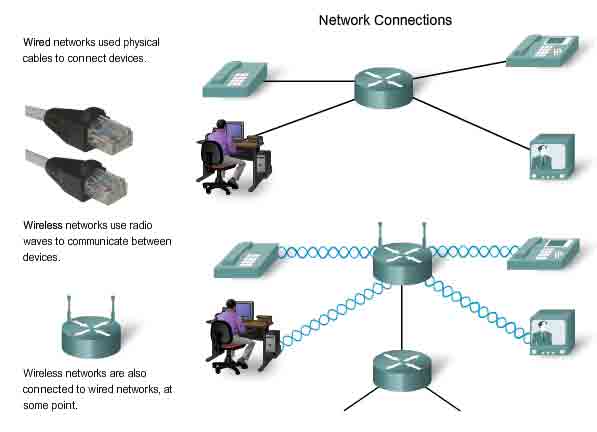
For a network to function, the devices must be interconnected. Network connections can be wired or wireless. In wired connections, the medium is either copper, which carries electrical signals, or optical fiber, which carries light signals. In wireless connections, the medium is the Earth's atmosphere, or space, and the signals are microwaves. Copper medium includes cables, such as twisted pair telephone wire, coaxial cable, or most commonly, what is known as Category 5 Unshielded Twisted Pair (UTP) cable. Optical fibers, thin strands of glass or plastic that carry light signals, are another form of internetworking media. Wireless media may include the home wireless connection between a wireless router and a computer with a wireless network card, the terrestrial wireless connection between two ground stations, or the communication between devices on earth and satellites. In a typical journey across the Internet, a message may travel across a variety of media.
Human beings often seek to send and receive a variety of messages using computer applications; these applications require services to be provided by the network. Some of these services include the World Wide Web, e-mail, instant messaging, and IP Telephony. Devices interconnected by medium to provide services must be governed by rules, or protocols. In the chart, some common services and a protocol most directly associated with that service are listed. Protocols are the rules that the networked devices use to communicate with each other. The industry standard in internetworking today is a set of protocols called TCP/IP(Transmission Control Protocol/Internet Protocol). TCP/IP is used in home and business networks, as well as being the primary protocol of the Internet. It is TCP/IP protocols that specify the formatting, addressing and routing mechanisms that ensure our messages are delivered to the correct recipient.
The Messages
In the first step of its journey from the computer to its destination, our instant message gets converted into a format that can be transmitted on the network. All types of messages must be converted to bits, binary coded digital signals, before being sent to their destinations. This is true no matter what the original message format was: text, video, voice, or computer data. Once our instant message is converted to bits, it is ready to be sent onto the network for delivery.
The Devices
To begin to understand the robustness and complexity of the interconnected networks that make up the Internet, it is necessary to start with the basics. Take the example of sending the text message using an instant messaging program on a computer. When we think of using network services, we usually think of using a computer to access them. But, a computer is only one type of device that can send and receive messages over a network. Many other types of devices can also be connected to the network to participate in network services. Among these devices are telephones, cameras, music systems, printers and game consoles.
In addition to the computer, there are numerous other components that make it possible for our instant message to be directed across the miles of wires, underground cables, airwaves and satellite stations that might exist between the source and destination devices. One of the critical components in any size network is the router. A router joins two or more networks, like a home network and the Internet, and passes information from one network to another. Routers in a network work to ensure that the message gets to its destination in the most efficient and quickest manner.
The Medium
To send our instant message to its destination, the computer must be connected to a wired or wireless local network. Local networks can be installed in homes or businesses, where they enable computers and other devices to share information with each other and to use a common connection to the Internet.
Wireless networks allow the use of networked devices anywhere in an office or home, even outdoors. Outside the office or home, wireless networking is available in public hotspots, such as coffee shops, businesses, hotel rooms, and airports.
Many installed networks use wires to provide connectivity. Ethernet is the most common wired internetworking technology found today. The wires, called cables, connect the computers and other devices that make up the networks. Wired networks are best for moving large amounts of data at high speeds, such as are required to support professional-quality multimedia.
The Services
Network services are computer programs that support the human network. Distributed on devices throughout the network, these services facilitate online communication tools such as e-mail, bulletin/discussion boards, chat rooms, and instant messaging. In the case of instant messaging, for example, an instant messaging service, provided by devices in the cloud, must be accessible to both the sender and recipient.
The Rules
Important aspects of networks that are neither devices nor media are rules, or protocols. These rules are the standards and protocols that specify how the messages are sent, how they are directed through the network, and how they are interpreted at the destination devices. For example, in the case of Jabber instant messaging, the XMPP, TCP, and IP protocols are all important sets of rules that enable our communication to occur.
The Network architecture:
Networks must support a wide range of applications and services, as well as operate over many different types of physical infrastructures. The term network architecture, in this context, refers to both the technologies that support the infrastructure and the programmed services and protocols that move the messages across that infrastructure. As the Internet, and networks in general, evolve, we are discovering that there are four basic characteristics that the underlying architectures need to address in order to meet user expectations: fault tolerance, scalability, quality of service, and security.
Fault Tolerance
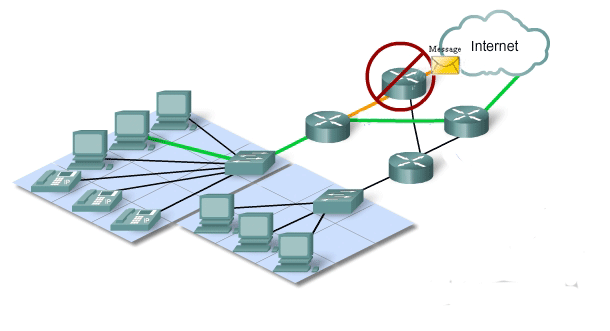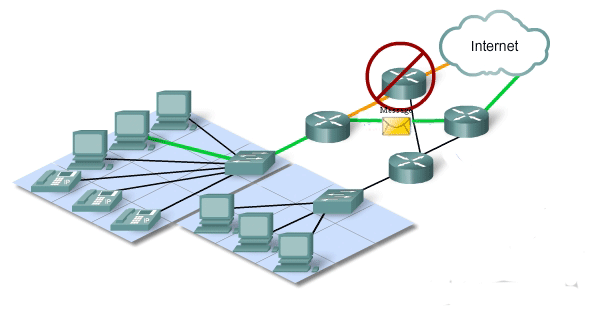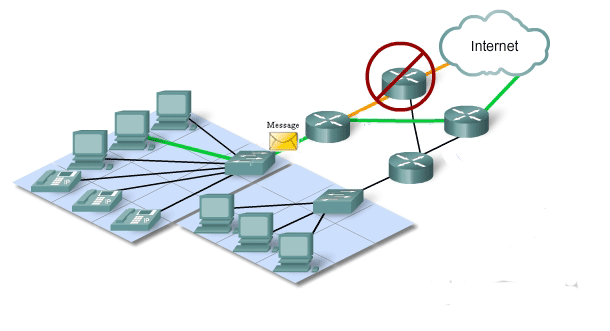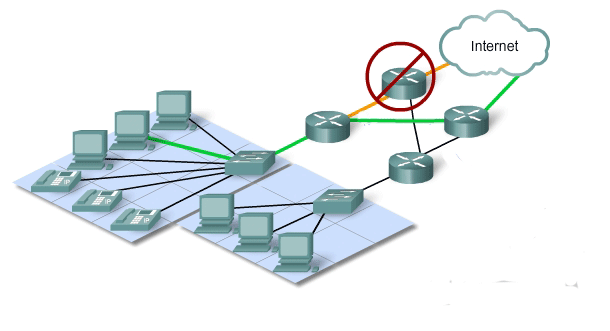
The expectation that the Internet is always available to the millions of users who rely on it requires a network architecture that is designed and built to be fault tolerant. A fault tolerant network is one that limits the impact of a hardware or software failure and can recover quickly when such a failure occurs. These networks depend on redundant links, or paths, between the source and destination of a message. If one link or path fails, processes ensure that messages can be instantly routed over a different link transparent to the users on either end. Both the physical infrastructures and the logical processes that direct the messages through the network are designed to accommodate this redundancy. This is a basic premise of the architecture of current networks.
Scalability
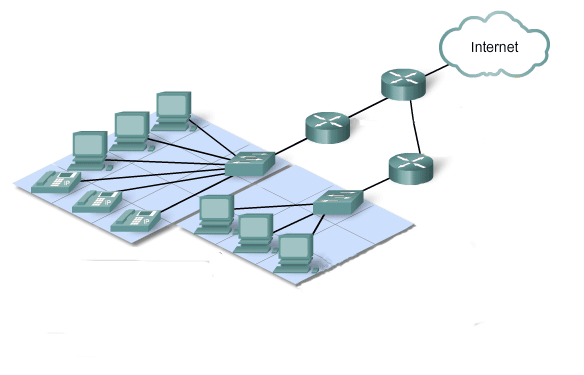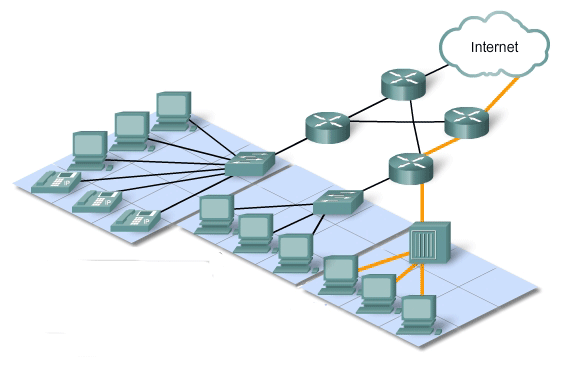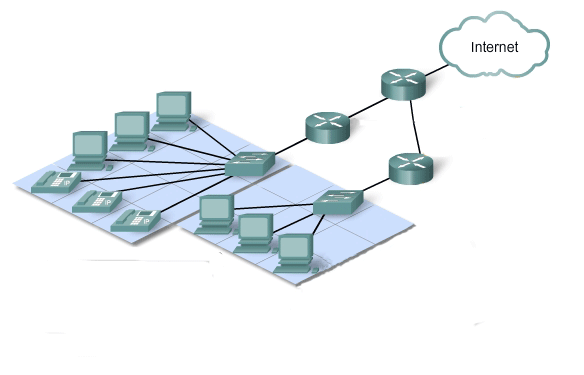
A scalable network can expand quickly to support new users and applications without impacting the performance of the service being delivered to existing users. Thousands of new users and service providers connect to the Internet each week. The ability of the network to support these new interconnections depends on a hierarchical layered design for the underlying physical infrastructure and logical architecture. The operation at each layer enables users or service providers to be inserted without causing disruption to the entire network. Technology developments are constantly increasing the message carrying capabilities and performance of the physical infrastructure components at every layer. These developments, along with new methods to identify and locate individual users within an internetwork, are enabling the Internet to keep pace with user demand.
Quality of Service (QoS)
The Internet is currently providing an acceptable level of fault tolerance and scalability for its users. But new applications available to users over internetworks create higher expectations for the quality of the delivered services. Voice and live video transmissions require a level of consistent quality and uninterrupted delivery that was not necessary for traditional computer applications. Quality of these services is measured against the quality of experiencing the same audio or video presentation in person. Traditional voice and video networks are designed to support a single type of transmission, and are therefore able to produce an acceptable level of quality. New requirements to support this quality of service over a converged internetworking are changing the way network architectures are designed and implemented.
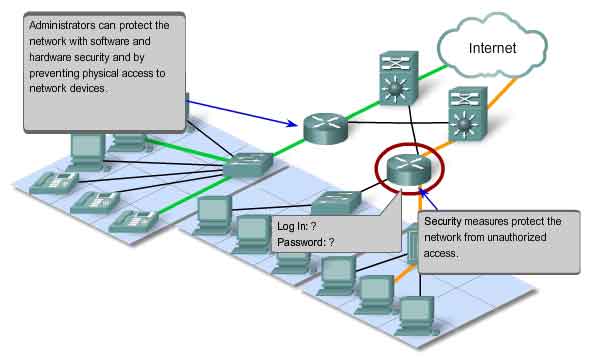
Security
The Internet has evolved from a tightly controlled internetwork of educational and government organizations to a widely accessible means for transmission of business and personal communications. As a result, the security requirements of the network have changed. The security and privacy expectations that result from the use of internetworks to exchange confidential and business critical information exceed what the current architecture can deliver. Rapid expansion in communication areas that were not served by traditional data networks is increasing the need to embed security into the network architecture. As a result, much effort is being devoted to this area of research and development. In the meantime, many tools and procedures are being implemented to combat inherent security flaws in the network architecture.
Fault Tolerant Network Architecture
The Internet, in its early inception, was the result of research funded by the United States Department of Defense (DoD). Its primary goal was to have a communications medium that could withstand the destruction of numerous sites and transmission facilities without disruption of service. It only follows that fault tolerance was the focus of the effort of the initial internetwork design work. Early network researchers looked at the existing communication networks, which were primarily for the transmission of voice traffic, to determine what could be done to improve the fault tolerance level.
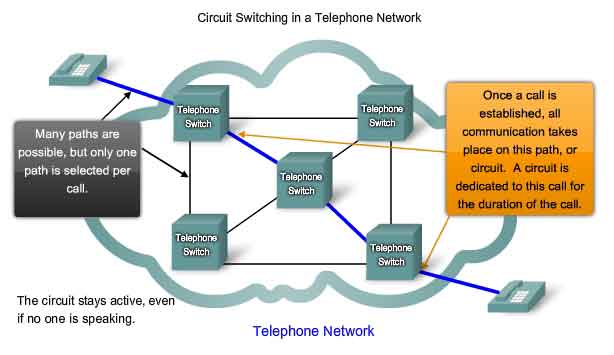
Circuit Switched Connection-oriented Networks
To understand the challenge that the DoD researchers were faced with, it is necessary to look at how early telephone systems work. When a person makes a call using a traditional telephone set, the call first goes through a setup process, where all of the telephone switching locations between the person and the phone set that they are calling are identified. A temporary path, or circuit, is created through the various switching locations to use for the duration of the telephone call. If any link or device participating in the circuit fails, the call is dropped. To reconnect, a new call must be made, and a new circuit created between the source telephone set and the destination. This type of connection-oriented network is called a circuit-switched network. Early circuit switched networks did not dynamically recreate dropped circuits. In order to recover from failure, new calls had to be initiated and new circuits built end-to-end. Many circuit switched networks give priority to maintaining existing circuit connections, at the expense of new circuit requests. In this type of connection-oriented network, once a circuit is established, even if no communication is occurring between the persons on either end of the call, the circuit remains connected and resources reserved until one of the parties disconnects the call. Since there is a finite capacity to create new circuits, it is possible to occasionally get a message that all circuits are busy and a call cannot be placed. The cost to create many alternate paths with enough capacity to support a large number of simultaneous circuits, and the technologies necessary to dynamically recreate dropped circuits in the event of a failure, led the DoD to consider other types of networks.
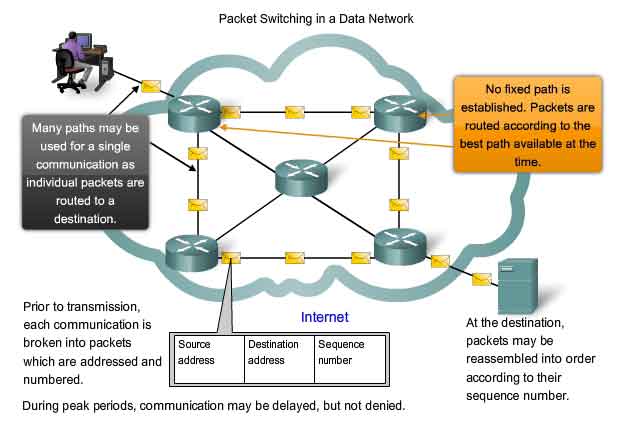
Packet Switched Connectionless Networks
In the search for a network that could withstand the loss of a significant amount of its transmission and switching facilities, the early Internet designers reevaluated early research regarding packet switched networks. The premise for this type of networks is that a single message can be broken into multiple message blocks. Individual blocks containing addressing information indicate both their origination point and their final destination. Using this embedded information, these message blocks, called packets, can be sent through the network along various paths, and can be reassembled into the original message upon reaching their destination.
Utilizing Packets
The devices within the network itself are unaware of the content of the individual packets, only visible is the address of the final destination and the next device in the path to that destination. No reserved circuit is built between sender and receiver. Each packet is sent independently from one switching location to another. At each location, a routing decision is made as to which path to use to forward the packet towards its final destination. If a previously used path is no longer available, the routing function can dynamically choose the next best available path. Because the messages are sent in pieces, rather than as a single complete message, the few packets that may be lost in the advent of a failure can be retransmitted to the destination along a different path. In many cases, the destination device is unaware that any failure or rerouting has occurred.
Packet-switched Connectionless Networks
The DoD researchers realized that a packet switched connectionless network had the features necessary to support a resilient, fault tolerant network architecture. The need for a single, reserved circuit from end-to-end does not exist in a packet switched network. Any piece of a message can be sent through the network using any available path. Packets containing pieces of messages from different sources can travel the network at the same time. The problem of underutilized or idle circuits is eliminated -- all available resources can be used at any time to deliver packets to their final destination. By providing a method to dynamically use redundant paths, without intervention by the user, the Internet has become a fault tolerant, scalable method of communications.
Connection-oriented Networks
Although packet-switched connectionless networks met the needs of the DoD, and continue to be the primary infrastructure for today's Internet, there are some benefits to a connection-oriented system like the circuit-switched telephone system. Because resources at the various switching locations are dedicated to providing a finite number of circuits, the quality and consistency of messages transmitted across a connection-oriented network can be guaranteed. Another benefit is that the provider of the service can charge the users of the network for the period of time that the connection is active. The ability to charge users for active connections through the network is a fundamental premise of the telecommunication service industry.
A Scalable Network Architecture
The fact that the Internet is able to expand at the rate that it is, without seriously impacting the performance experienced by individual users, is a function of the design of the protocols and underlying technologies on which it is built. The Internet, which is actually a collection of interconnected private and public networks, has a hierarchical layered structure for addressing, for naming and for connectivity services. At each level or layer of the hierarchy, individual network operators maintain peering relationships with other operators at the same level. As a result, network traffic that is destined for local or regional services does not need to traverse to a central point for distribution. Common services can be duplicated in different regions, thereby keeping traffic off the higher level backbone networks.Although there is no single organization that regulates the Internet, the operators of the many individual networks that provide Internet connectivity cooperate to follow accepted standards and protocols. The adherence to standards enables the manufacturers of hardware and software to concentrate on product improvements in the areas of performance and capacity, knowing that the new products can integrate with and enhance the existing infrastructure. The current Internet architecture, while highly scalable, may not always be able to keep up with the pace of user demand. New protocols and addressing structures are under development to meet the increasing rate at which Internet applications and services are being added.
Providing Quality of Service
Networks must provide secure, predictable, measurable, and, at times, guaranteed services. The packet-switched network architecture does not guarantee that all packets that comprise a particular message will arrive on time, in their correct in order, or even that they will arrive at all. Networks also need mechanisms to manage congested network traffic. Congestion is caused when the demand on the network resources exceeds the available capacity. If all networks had infinite resources, there would not be a need to use QoS mechanisms to ensure quality of service. Unfortunately, that is not the case. There are some constraints on network resources that cannot be avoided. Constraints include technology limitations, costs, and the local availability of high-bandwidth service. Network bandwidth is the measure of the data carrying capacity of the network. When simultaneous communications are attempted across the network, the demand for network bandwidth can exceed its availability. The obvious fix for this situation is to increase the amount of available bandwidth. But, because of the previously stated constraints, this is not always possible. In most cases, when the volume of packets is greater than what can be transported across the network, devices queue the packets in memory until resources become available to transmit them. Queuing packets causes delay. If the number of packets to be queued continues to increase, the memory queues fill up and packets are dropped.
Achieving the required Quality of Service (QoS) by managing the delay and packet loss parameters on a network becomes the secret to a successful end-to-end application quality solution. Thus, ensuring QoS requires a set of techniques to manage the utilization of network resources. In order to maintain a high quality of service for applications that require it, it is necessary to prioritize which types of data packets must be delivered at the expense of other types of packets that can be delayed or dropped.
Classification
Ideally, we would like to assign a precise priority for each type of communication. Currently, this is neither practical nor possible. Therefore, we classify applications in categories based on specific quality of service requirements. To create QoS classifications of data, we use a combination of communication characteristics and the relative importance assigned to the application. We then treat all data within the same classification according to the same rules. For example, communication that is time-sensitive or important would be classified differently from communication that can wait or is of lesser importance.
Assigning priorities
The characteristics of the information being communicated also affect its management. For example, the delivery of a movie uses a relatively large amount of network resources when it is delivered continuously without interruption. Other types of service - e-mail, for example - are not nearly as demanding on the network. In one company, an administrator might decide to allocate the greatest share of the network resources to the movie, believing that this is the priority for his customers. This administrator may decide that the impact will be minimal if e-mail users have to wait a few additional seconds for their e-mail to arrive. In another company, the quality of a video stream is not as important as critical process control information that operates the manufacturing machinery.
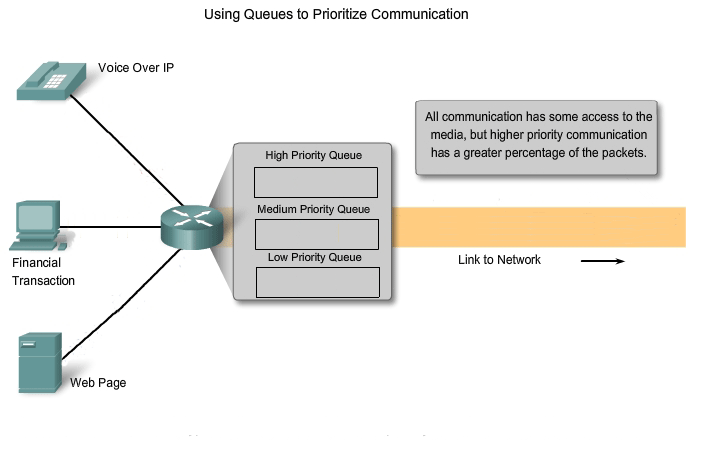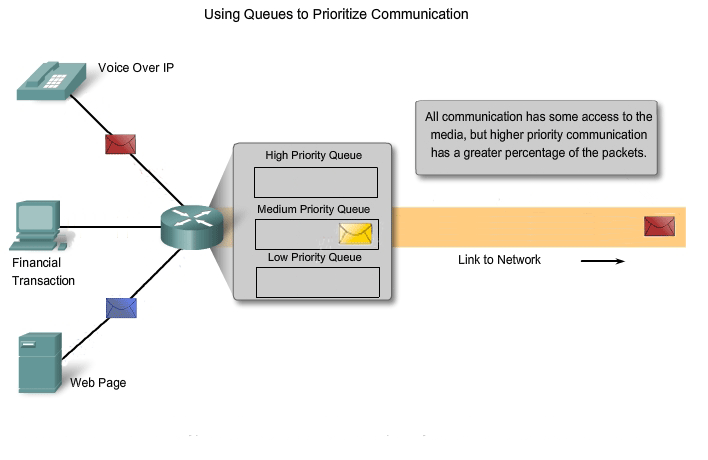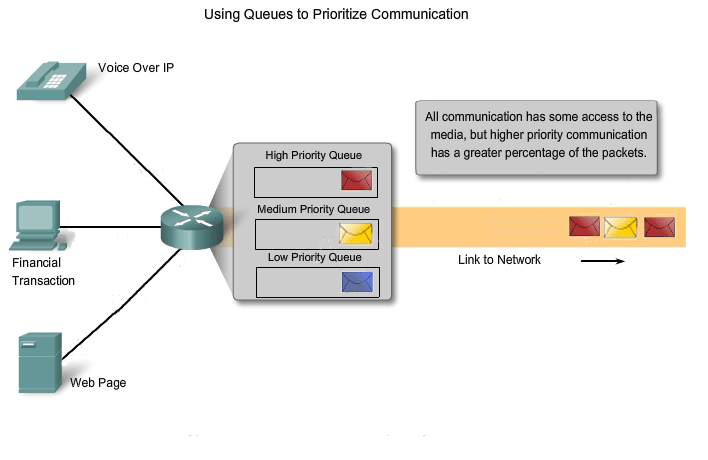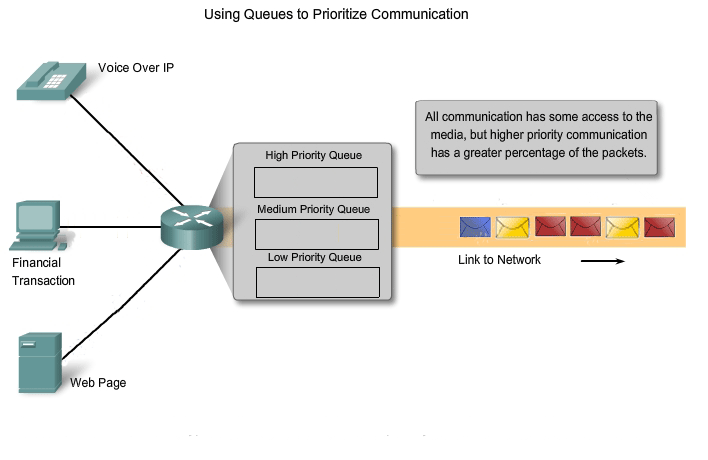
QoS mechanisms enable the establishment of queue management strategies that enforce priorities for different classifications of application data. Without properly designed and implemented QoS mechanisms, data packets will be dropped without consideration of the application characteristics or priority. Examples of priority decisions for an organization might include:
-
Time-sensitive communication - increase priority for services like telephony or video distribution.
- Non time-sensitive communication - decrease priority for web page retrieval or e-mail.
- High importance to organization - increase priority for production control or business transaction data.
- Undesirable communication - decrease priority or block unwanted activity, like peer-to-peer file sharing or live entertainment.
The Quality of Service a network can offer is a vital issue, and in some situations, it is crucial. Imagine the consequences of a dropped distress call to an emergency response center, or of a lost control signal to an automated piece of heavy machinery. A key responsibility for the network managers in an organization is to establish a Quality of Service policy and ensure that the mechanisms are in place to meet that goal.
Providing Network Security
The network infrastructure, services, and the data contained on network attached computers are crucial personal and business assets. Compromising the integrity of these assets could have serious business and financial repercussions. Consequences of a network security breach could include:
-
Network outage that prevents communications and transactions occurring, with consequent loss of business
- Misdirection and loss of personal or business funds
- Company intellectual property (research ideas, patents or designs) that is stolen and used by a competitor
- Customer contract details that become known to competitors or made public, resulting in a loss of market confidence in the business
A lack of public trust in the business's privacy, confidentiality, and integrity levels may lead to loss of sales and eventual company failure. There are two types of network security concerns that must be addressed to prevent serious consequences: network infrastructure security and content security. Securing a network infrastructure includes the physical securing of devices that provide network connectivity and preventing unauthorized access to the management software that resides on them. Content security refers to protecting the information contained within the packets being transmitted over the network and the information stored on network attached devices. When transmitting information over the Internet or other network, the content of the individual packets is not readily known to the devices and facilities through which the packets travel. Tools to provide security for the content of individual messages must be implemented on top of the underlying protocols which govern how packets are formatted, addressed and delivered. Because the reassembly and interpretation of the content is delegated to programs running on the individual source and destination systems, many of the security tools and protocols must be implemented on those systems as well.
Security measures taken in a network should:
-
Prevent unauthorized disclosure or theft of information
- Prevent unauthorized modification of information
- Prevent Denial of Service
Means to achieve these goals include:
-
Ensuring confidentiality
- Maintaining communication integrity
- Ensuring availability
Ensuring Confidentiality
Data privacy is maintained by allowing only the intended and authorized recipients - individuals, processes, or devices - to read the data. Having a strong system for user authentication, enforcing passwords that are difficult to guess, and requiring users to change them frequently helps restrict access to communications and to data stored on network attached devices. Where appropriate, encrypting content ensures confidentiality and minimizes unauthorized disclosure or theft of information.
Maintaining Communication Integrity
Data integrity means having the assurance that the information has not been altered in transmission, from origin to destination. Data integrity can be compromised when information has been corrupted - willfully or accidentally - before the intended recipient receives it. Source integrity is the assurance that the identity of the sender has been validated. Source integrity is compromised when a user or device fakes its identity and supplies incorrect information to a recipient. The use ofdigital signatures, hashing algorithms and checksum mechanisms are ways to provide source and data integrity across a network to prevent unauthorized modification of information.
Ensuring Availability
Ensuring confidentiality and integrity are irrelevant if network resources become over burdened, or not available at all. Availability means having the assurance of timely and reliable access to data services for authorized users. Resources can be unavailable during a Denial of Service (DoS) attack or due to the spread of a computer virus. Network firewall devices, along with desktop and server anti-virus software can ensure system reliability and the robustness to detect, repel, and cope with such attacks. Building fully redundant network infrastructures, with few single points of failure, can reduce the impact of these threats. The result of the implementation of measures to improve both the quality of service and the security of network communications is an increase in the complexity of the underlying network platform. As the Internet continues to expand to offer more and more new services, its future depends on new, more robust internetworking architectures being developed that include all four characteristics: fault tolerance, scalability, quality of service, and security.